Cybersecurity News
20 hours ago
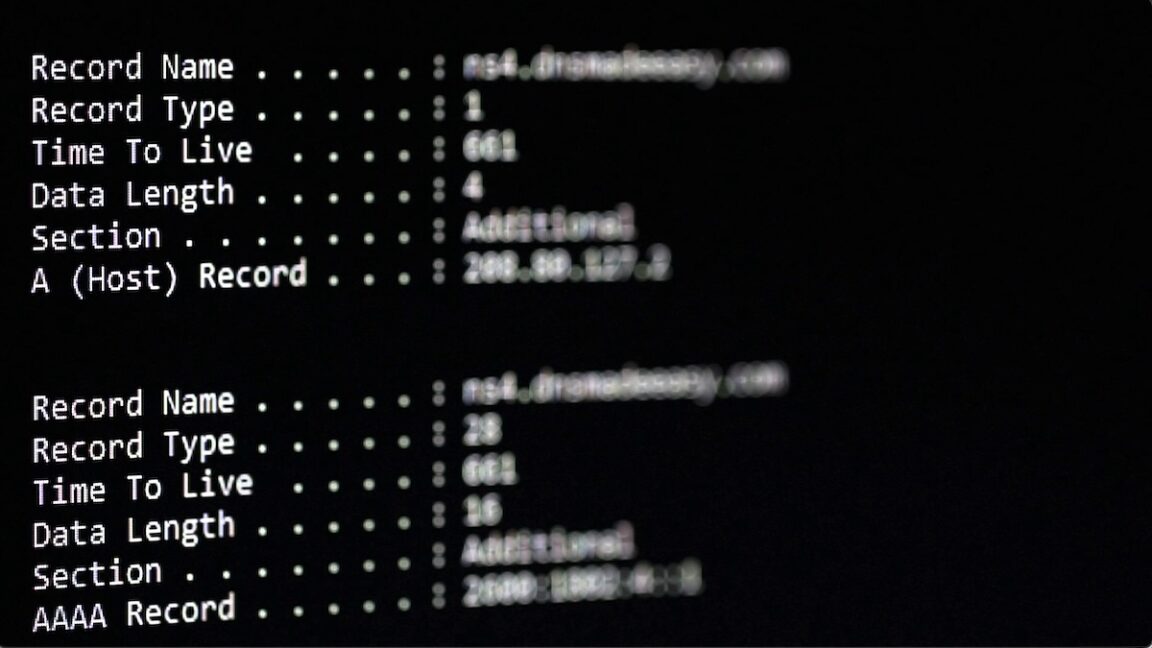
A sophisticated new attack vector where malicious actors are hiding malware inside DNS records, exploiting a critical blind spot in most organizations’ security infrastructure. This technique transfor...
GB Hackers
1 day ago
Hackers Use DNS Queries to Evade Defenses and Exfiltrate Data
Cybercriminals are increasingly exploiting the Domain Name System (DNS) to bypass corporate security measures and steal sensitive data, ac...
Cybersecurity News
1 day ago
Cybercriminals are increasingly leveraging DNS (Domain Name System) tunneling to establish covert communication channels that bypass traditional network security measures.
This sophisticated technique...
Ars Technica
2 days ago
Hackers are stashing malware in a place that’s largely out of the reach of most defenses—inside domain name system (DNS) records that map domain names to their corresponding numerical IP addresses.
Th...
Wired
1 day ago
Hackers are stashingmalware in a place that’s largely out of the reach of most defenses—inside domain name system (DNS) records that map domain names to their corresponding numerical IP addresses.
The...