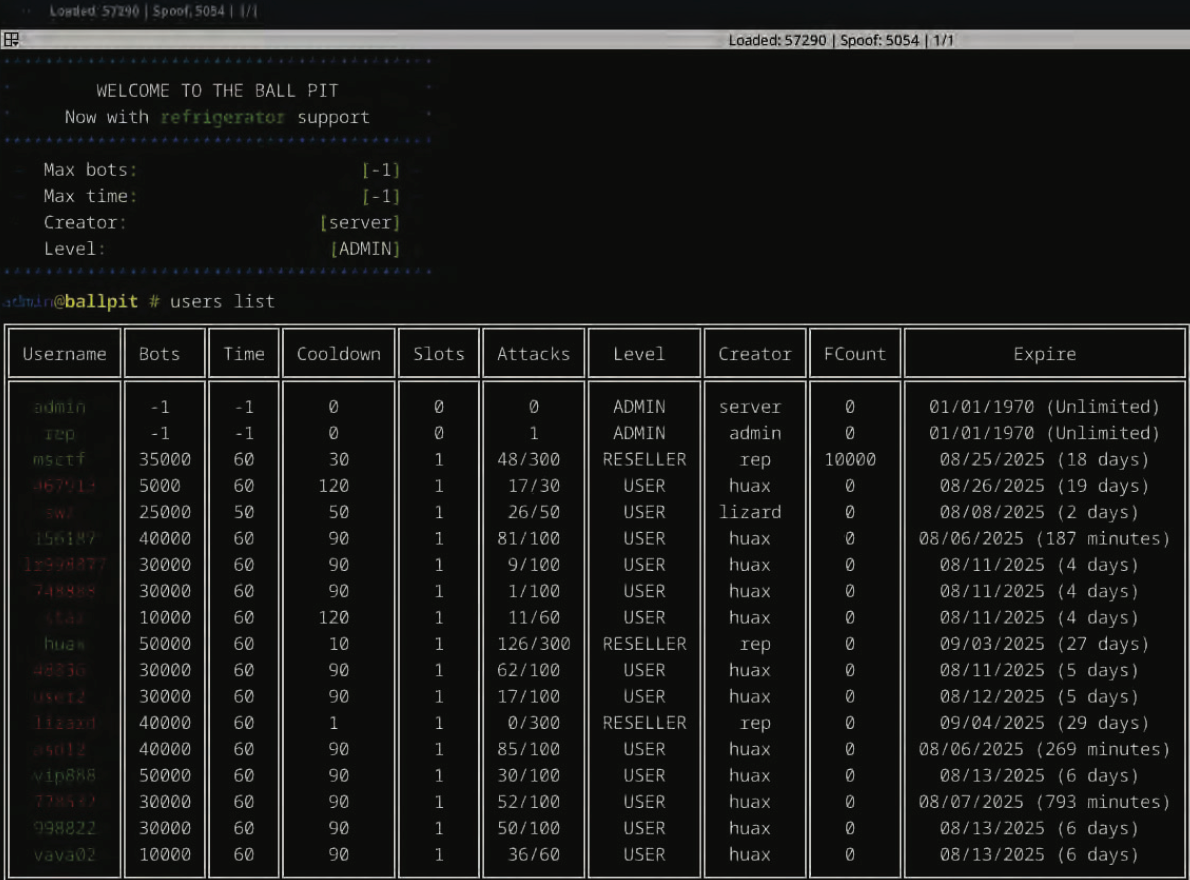
Rapper Bot was ‘one of the most powerful DDoS botnets to ever exist’ – now it’s done and dusted
Threat Score:
76
5 articles
100.0% similarity
10 hours ago
Article Timeline
5 articles
Click to navigate
Related Articles
5 articles
1
Score
Read more
73
100.0% similarity
2
DOJ Charges 22-Year-Old for Running RapperBot Botnet Behind 370,000 DDoS Attacks
Score
Read more
71
97.0% similarity
3
Oregon Man Charged in Global “Rapper Bot” DDoS-For-Hire Scheme
Score
Read more
70
100.0% similarity
4
Feds charge alleged administrator of ‘sophisticated’ Rapper Bot botnet
Score
Read more
61
100.0% similarity
5
Oregon Man Charged in ‘Rapper Bot’ DDoS Service
Score
Read more
56
97.0% similarity